In a post titled Government Wiretaps in U.S. Internet Providers Infiltrated by Chinese Hackers, Matt Johnasen writes that major US broadband providers have had their court-authorized wiretap backdoor to monitor internet access exploited by Chinese Hackers, who ‘may have had access for months to systems used for lawful wiretapping request’1. Apparently US broadband providers such as AT&T, Verizon, and Lumen Technologies are required to have backdoor access to internet traffic to allow authorized collections of users internet traffic when investigations are occurring. While the intent of these backdoor access tap points are meant to be used for good, when an another entry, exit, or dup point is written into code, good security practices should indicate this point will be found by people with ill intent and they will try to exploit it. Below is the lawful flow of utilizing the backdoor intercept method that was exploited.
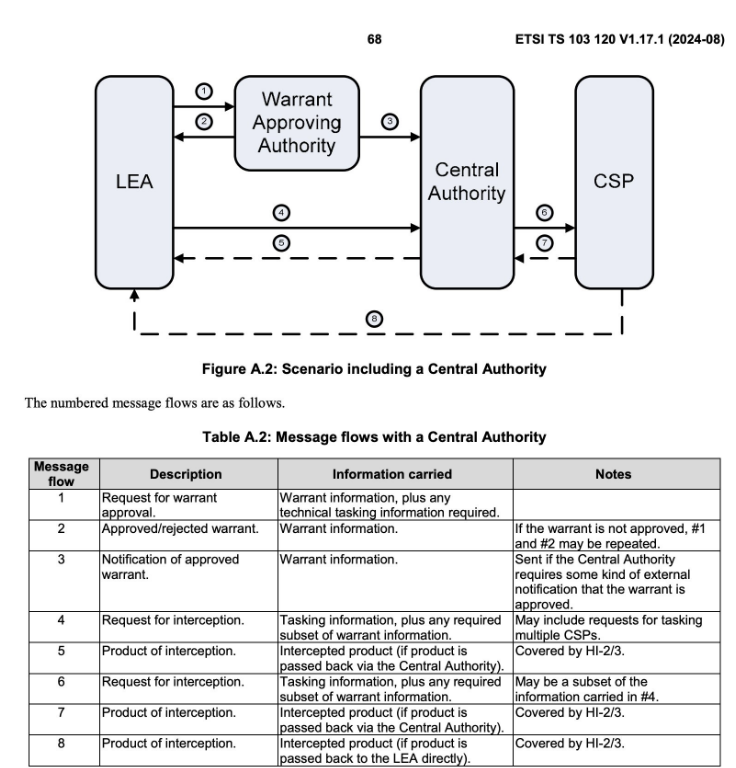
When designing, developing, integrating, troubleshooting, and finalizing space systems cyber security should be at the forefront of the process. As a designer ensuring you know where all the entry and exit points to your system and code is crucial and should be protected appropriately. Also, as the space industry expands we can fully expect to receive requirements such as what was described above. These should be handled very carefully to ensure the security of such requirements.