Space is becoming an increasingly important domain, but it is also getting increasingly congested and particularly vulnerable to a variety of cyber vulnerabilities and attacks. And, because of the lack of notice, the speed with which an adversary may launch an assault, the difficulties of attribution, and the complications connected with carrying out a proportionate response, these cyber-attacks constitute a substantial and complicated problem.
As previously stated in class, space systems are divided into four segments: the space segment, the link segment, the user segment, and the ground segment.
What are some of the tactics used to attack space systems?
These strategies differ based on the point of entrance or objective. The figure below is from a paper released by The Aerospace Corporation and depicts how threat actors approach distinct segments.
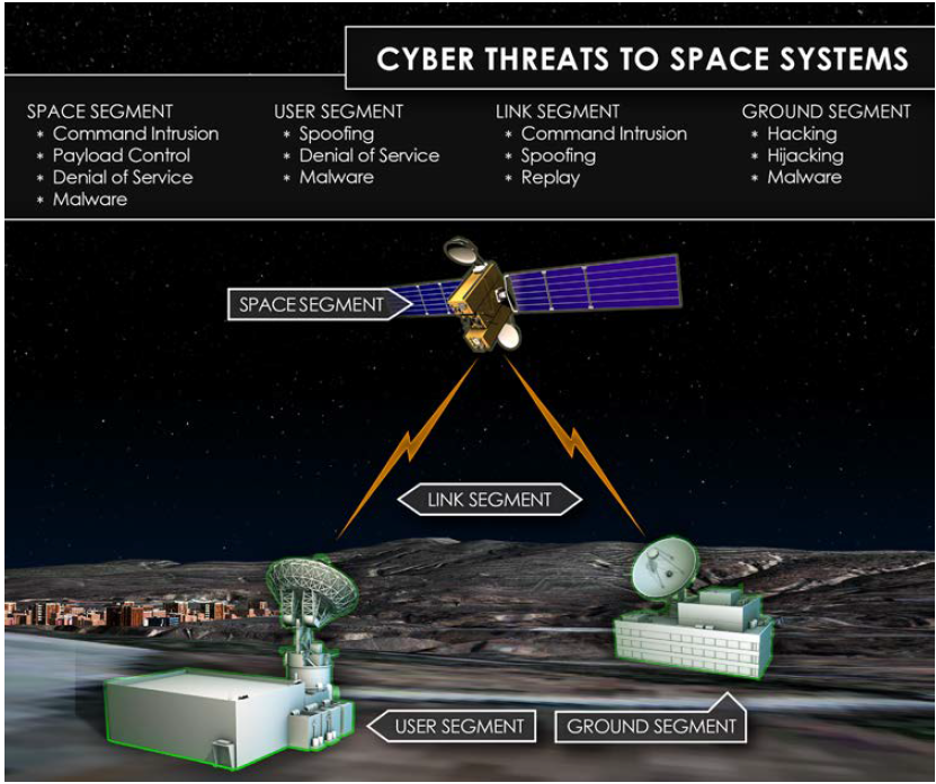
Figure 1: Different Segments of space systems are prone to different types of attack. Illustration courtesy National Air, Space, and Intelligence Center (NASIC)
The United States government has highlighted some of the most serious risks to space systems, and the White House’s executive order on boosting cybersecurity for IT and operational technology (OT) highlights an important part of the space system.
“These systems are at the intersection of cyber and physical worlds,” says Kevin Coggins, vice president and head of Booz Allen’s positioning, navigation, and timing (PNT) business. “You must protect the threat surface of the physical systems as well as their network connection”.
ESTABLISH FRAMEWORK
Open frameworks are the cornerstone of flexible systems and the starting point for improved protection techniques.
Open Systems Architecture
A starting point for next-generation engineering in the confluence of space security and cybersecurity is the migration to open systems architecture. Through open standards and reusable components, open frameworks allow organizations to:
– Effectively modernize legacy systems
– Effectively incorporate security into new data platforms
– Promote ongoing innovation while adhering to the technical standard
IT/OT Best Practices
Space systems, which combine OT and IT, require cyber defenses akin to those found in industrial control systems and other operational technologies, such as automated procedures. All government IT systems need to be subject to mandatory precautions, such as:
– Architectures with zero trust
– Continuous monitoring of secure cloud settings
– Interoperability over simplified networks
REFERENCES