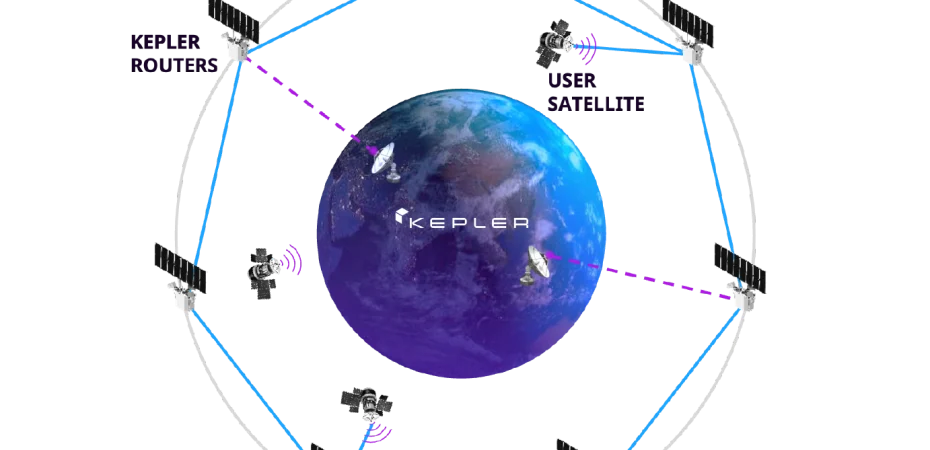
Emergent small satellite (SmallSat) operator Kepler Communications has raised 92 million dollars to begin work on deploying its optical data-relay constellation beginning in 2025. It currently operates a constellation of 19 SmallSats and plans to expand to 140 satellites in the future, providing a communication link to other earth orbiting satellites. Their goal with this constellation is to create an ‘Internet for Space’ that enables earth observing, defense and intelligence, and human spaceflight operators to connect in real time to their systems to receive updates. This unique ‘On Demand’ capability is achieved through the optical relay crosslinks connecting each satellite to its neighbor, creating a dynamic mesh with complex handoffs occurring as links are lost and ground stations fade from view. Utilizing the optical relay allows Kepler Communications to pass data at 2.5 Gbps, with an in-development Edge Compute that will allow data to be processed on orbit to reduce latency for customers, all of which are pushing the limits of what was thought possible.
While these unique capabilities represent large advancements in the industry, it opens new risks for nefarious cyber actors to exploit if not secured. The first vulnerability this architecture presents is an always connected satellite constellation. Though the constant data stream presents advantages for operators to better monitor systems and receive mission data, it also allows for attackers who once had mere minutes to attempt to penetrate a system the now constant connection to learn new vulnerabilities and adjust methods on the fly. This new extended connectivity approaches ground based systems in terms of time available to attack but lacks the advancements and upgrades in both hardware and software that ground systems are accustomed to.
Additionally, the interconnected nature of the constellation opens them up to rapid lateral attack expansion stemming from the optical crosslinks. With many satellites relying on a ground connection to transmit data, any potential attack is isolated to a small number of satellites that are either connected or within a close enough proximity to fall victim to additional sophisticated attacks. However, with an interconnected relay, an attacker can quickly maneuver to any connected satellite, affecting not only the Kepler relays but also any satellite that is relying on them for mission data transfer. This creates a massive surface area for an attacker to compromise and opens an innumerable number of places to hide from detection and removal once initial access is attained.
Although the satellite-to-satellite communications for this constellation are optical relays, the ground connection still largely relies on an RF link antenna to downlink the data to the ground. This is not out of the ordinary for most satellites, however it does negate the more secure optical communications and opens the constellation up to traditional jamming and RF link attacks typical in other systems. Future iterations of this constellation may baseline the optical communications to ground as standard, but will almost certainly rely on backup RF links for contingency support.
While Kepler Communications is the focus of this analysis, they are not the only industry player vulnerable to these types of exploitations. Increasingly, large corporations are adopting this expansive and interconnected constellation model due to the advantages it offers in terms of data latency, redundancy, and overall profitability. Companies like SpaceX, OneWeb and Telesat are all operating interconnected constellations of hundreds to thousands of SmallSats, numbers that were unheard of just a few years ago. With the rapid pace of change towards the proliferated architecture, special attention needs to be put towards securing these systems from cyber threats. Otherwise, the advanced systems being developed today risk becoming an Achilles heel to the space community and users at large.
https://kepler.space/network/
https://www.mdpi.com/2226-4310/9/5/234